Connect to Blocked Ports with SSH Tunneling
SSH Tunneling – Get Through Your Firewall to Other Ports

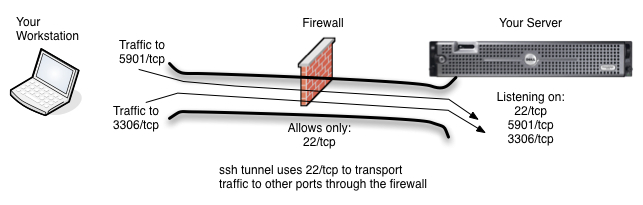
Typical Scenario is that only the ssh port (tcp/22) and http (tcp/80) are allowed into a machine. All other traffic is blocked.
Do you have a server on the other side of a firewall that you can ssh to, but to which you cannot reach on other ports. Let’s imagine, for example, that your server has ports 80/tcp and 22/tcp open, but you want to be able to get to your database port (3306/tcp) or your vnc port (5901/tcp) which are blocked by the firewall. Grr. What can you do? Use ssh tunneling, of course.
SSH Tunneling is Similar to VPN
Ssh allows you to tunnel your communication to other ports and services on your server through your ssh connection to the server. This means that traffic that would normally be blocked by your firewall or iptables can now reach its destination. This of course, all assumes that you have a login to the server and are able to ssh to it from your network or internet location.
SSH Tunneling Uses a Local Port
The idea behind ssh tunneling is that you know which port(s) you want to access on the server and that you also setup a local port on your workstation for you to connect to on your side of the tunnel. When using SSH Tunneling, you will direct your client applications, in this example case MySQL Workbench and VNC Viewer, to the local ports on your workstation which you configured in your ssh client. SSH will then transport the traffic to the local port through its tunnel to the server port you are hoping to reach.
Ssh Command Line (CLI) Port Configuration
When using ssh from the command line in a linux, unix, OSX or other command line environment, you will use the -L option to map local ports to remote ports on the server. In the example below, Mary is logging in to server1.uptimemadeeasy.com with ssh and is mapping local port 8675 on her workstation to the MySQL port (tcp/3306) on the server. Note that the name localhost is in reference to server1.uptimemadeeasy.com.
ssh -l mary server1.uptimemadeeasy.com -L 8675:localhost:3306
Mary will then supply the password when requested and she will notice with netstat -an that port 8675 on her local workstation is now being used. She can then point her MySQL Workbench client at her local machine (localhost) port 8675. Her traffic to her local port 8675 will then be transported through her ssh tunnel to the server port 3306.
Mary can now verify that her local port (8675) is listening locally using netstat:
$ netstat -an | grep 8675
TCP 127.0.0.1:8675 0.0.0.0:0 LISTENING
TCP [::1]:8675 [::]:0 LISTENING
We get output telling us that the local workstation is now listening on port 8675 on both ipv4 and ipv6.
What if I Want to Ssh Tunnel to Multiple Ports
Frequently, if you are tunneling to one port over ssh, you will likely want to tunnel to multiple ports. In these cases, just supply additional -L options to the end of the command
ssh -l jstaten www.uptimemadeeasy.com -L 8675:localhost:3306 -L 8002:localhost:5901
With both of these ports mapped, you can communicate to either the MySQL Server (port 3306) and the VNC Server (port 5901)
Ssh Tunneling using Windows and Putty
So that’s great that we can use the command line for ssh tunneling, but what if my workstation is windows? In this case, find an ssh client that supports tunneling such as the ever-popular putty ssh client.
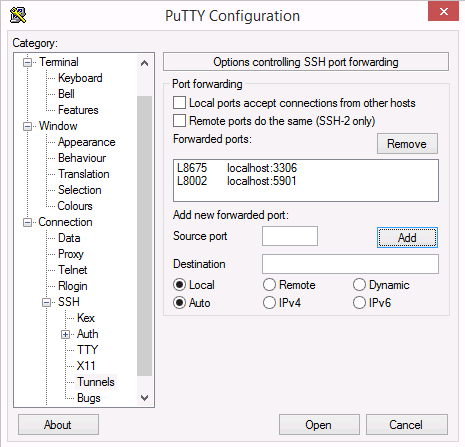
To setup ssh tunneling in putty:
- First, on the session category in the left column, setup your host with ssh and save it.
- With that host highlighted, change to the Connection / SSH Tunnels Category in the left column and setup the ports as shown in the image to the right. the L8675 specifies that the 8675 is the Local port on your workstation
- Third, go back to the session category on the left column and save your host again so that the tunnel configuration will persist.
- Finally, hit the open button and login. It should ask you for you password and then it will map your local ports to the foreign ports on the server. You should now be able to connect your clients (MySQL or VNC or other) to the ports on localhost:8675, localhost:8002 in this example or whatever local ports you configured on your machine.
Wow, How Do I Disable Ssh Tunneling
So, now that you’ve read this article, you are beginning to see how cool and how dangerous ssh tunneling can be. If you are scared of the possibilities, you are probably asking: How can I disable ssh tunneling? This is pretty simple. The default is on, of course, but you can edit the sshd_config file on your server and turn off forwarding. Just change the forwarding options to “No” or add these two lines:
AllowTcpForwarding no
X11Forwarding No
Now restart your ssh daemon and ssh tunneling should be disabled