psad: Intrusion Detection and Log Analysis with iptables
Source CipherDyne
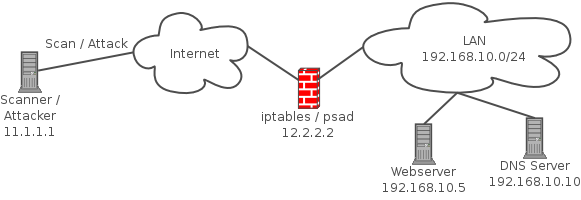
psad is a collection of three lightweight system daemons (two main daemons and one helper daemon) that run on Linux machines and analyze iptables log messages to detect port scans and other suspicious traffic. A typical deployment is to run psad on the iptables firewall where it has the fastest access to log data.
psad incorporates many signatures from the Snort intrusion detection system to detect probes for various backdoor programs (e.g. EvilFTP, GirlFriend, SubSeven), DDoS tools (mstream, shaft), and advanced port scans (FIN, NULL, XMAS) which are easily leveraged against a machine via nmap. When combined with fwsnort and the Netfilter string match extension, psad is capable of detecting many attacks described in the Snort rule set that involve application layer data. In addition, psad makes use of various packet header fields associated with TCP SYN packets to passively fingerprint remote operating systems (in a manner similar to p0f) from which scans originate. Further, psad can be integrated with Logstash, and also offers support for UFW firewalls [1]. For more information, see the complete list of features offered by psad.