Aria2 – L’outil de téléchargement ultra rapide
Source: korben.info
Les barbus du Linux le connaissent depuis longtemps, mais pour les autres, je vous explique rapidement. Tout d’abord Aria2 est sous licence GPL et tourne sans aucun souci sous Mac, Linux, Windows et même Android. L’outil est léger (il consomme peu de CPU et de mémoire), mais surtout très puissant puisqu’il gère en plus des liens classiques, les Metalink, ce qui lui permet de télécharger des fichiers en exploitant plusieurs connexions simultanées utilisant plusieurs sources et/ou protocoles différents.
Oui c’est fou ! Cela permet d’exploiter au maximum la bande passante que vous avez à votre disposition.
Aria2 supporte donc le HTTP, FTP, mais aussi Bittorrent avec toutes ses fonctionnalités (DHT, chiffrement PEX, URI magnétique, Web-Seeding, téléchargement sélectif, tracker UDP et le protocole Local Peer Discovery). Aria2 est aussi pilotable à distance (support RPC) et gère sans souci ce qui est droit d’accès, cookies, proxys…etc.
N’allez pas croire que Aria2 est un outil compliqué à prendre en main. Taratata, c’est au contraire très simple à piger, comme vous allez voir dans les exemples ci-dessous :
Pour télécharger simplement un fichier :
aria2c http://example.org/mylinux.iso
Pour télécharger un fichier à partir de 2 sources différentes (HTTP, FTP) :
aria2c http://a/f.iso ftp://b/f.iso
Pour télécharger un fichier à partir de 3 connexions de source différente (Torrent, FTP, HTTP) :
aria2c -Ttest.torrent "http://host1/file" "ftp://host2/file"
Si ça vous branche d’explorer un peu plus ses possibilités, la documentation est ici. Autrement, sachez aussi qu’il existe des interfaces graphiques pour Aria2 comme :
- webui-aria2: Interface navigateur
- uGet: Gestionnaire de téléchargement Linux
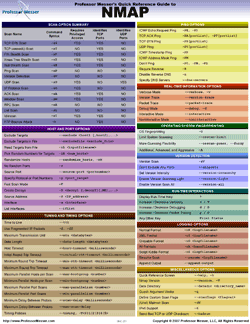 NMAP: One of the very first steps in any network reconnaissance mission is to reduce a (sometimes huge) set of IP ranges into a list of active or interesting hosts. Scanning every port of every single IP address is slow and usually unnecessary.
NMAP: One of the very first steps in any network reconnaissance mission is to reduce a (sometimes huge) set of IP ranges into a list of active or interesting hosts. Scanning every port of every single IP address is slow and usually unnecessary.